
The UN Trust Fund to End Violence against Women, which aims to prevent and address violence against women and girls by providing financial and technical support to local, national, and regional organizations working to eliminate gender-based violence and promote women’s rights, was linked to 115,000 records in a non-password-protected database that cybersecurity researcher Jeremiah Fowler found and reported to vpnMentor.
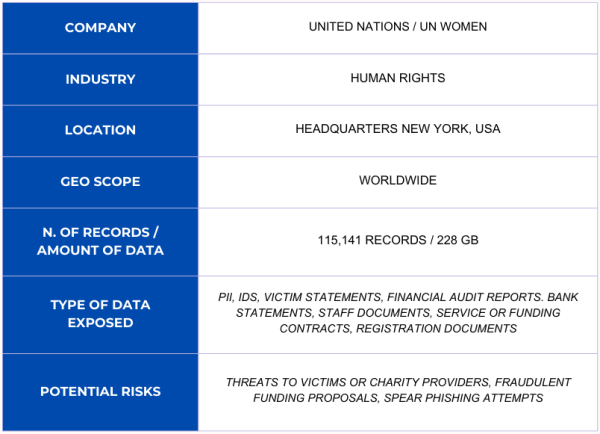
Financial reports and audits (including information about bank accounts), staff documentation, email addresses, contracts, certifications, registration paperwork, and much more were all included in the password-free, non-encrypted, clear text database. The database contained 115,141 files in various forms, including PDF, XML, JPG, PNG, and others, totaling 228 GB. I noticed a lot of documents that were classified as sensitive and shouldn’t have been released to the public. The internal UN application numbers of 1,611 civil society organizations, their eligibility for support, the status of their applications, whether they are local or national, and a variety of comprehensive responses on the groups’ missions were all included in a single.xls file.
Additionally, I spotted a large number of scanned ID cards, passports, and personnel directories from various organizations. Names, tax information, pay information, and work roles were all contained in the staff documentation. Additionally, there were records titled “victim success stories” or testimonies. Some of these included information about the individuals the programs assisted, including their names, email addresses, and personal experiences. One of the letters, for example, was allegedly written by a Chibok schoolgirl who was among the 276 people abducted by Boko Haram in 2014. For charity workers and the people they help or serve, the disclosure of sensitive information may have major privacy or safety repercussions.
The UN Trust Fund to End Violence Against Women and UN Women were mentioned in the archives. Examples included file names identifying the UN Women group, documents stamped with UN insignia, and reference letters sent directly to the UN. The next day, I restricted public access to the database after sending a responsible disclosure notification of my findings to UN Women and the general UN InfoSec address. “The reported vulnerability does not pertain to us (the United Nations Secretariat) and is for UN Women,” the UN Information Security team responded to my disclosure notice right away. Kindly notify UN WOMEN of the vulnerability.
It is unclear if the UN Women agency owned and operated the password-protected database or whether a third-party contractor was in charge of it, despite the documents indicating that the files belonged to the organization. Since only an internal forensic examination can determine such information, it is also uncertain how long the records were exposed or whether anyone else had access to them. At the time of publication, I never heard back from UN Women.
The UN Trust Fund to End Violence against Women (UN Trust Fund) provides to projects that show violence against women and girls can be systematically addressed, decreased, and, with perseverance, eradicated, according to their website. UN Women oversees the fund on behalf of the UN system. It offers funding to projects and groups that aim to eradicate gender-based violence, especially those headed by women. An estimated $225 million USD has been given by the fund to 670 projects across 140 nations and territories.
“UN Women has been made aware of various correspondences—circulated via email, websites, social media, regular mail, or facsimile—falsely stating that they are issued by, or in association with UN Women, the United Nations, and/or its officials,” reads an undated post on their website that issued a scam alert. These scams are deceptive and may aim to steal money and/or, frequently, personal information from the recipients of such mail. Usually, these frauds pose as respectable companies or people and ask for money in the form of application fees, dues, or other payments.
When a charity receives questionable requests for financial or personal information, especially if they are unsolicited payment requests, I would advise them to exercise extreme caution and vigilance. Carefully confirming the source of any communications is one method to achieve this. Verify that requests for information come from legitimate email addresses, and confirm any modifications to accounts or payment methods. Putting in place extra security measures might also lessen the likelihood that the company will fall victim to a cybercrime. Additionally, educating employees on fraud risks and typical social engineering techniques can assist stop unintentionally disclosing potentially private information to unauthorized parties.
In this instance, anyone with an internet connection could see thousands of internal documents. They weren’t secured with a password. Criminals may be able to learn about the organizations’ financial structures, key management, operational procedures, and other information from these records that may not have been meant for public consumption. Criminals could establish trust and possibly start focused spear phishing efforts with insider knowledge of identities, accounts, partnerships, and audit records—information that should not be known by anybody outside the company or UN. Theoretically, thieves might use or modify publicly available papers to obtain more personal data from employees and volunteers of charities.
Numerous charitable organizations function in nations and areas where there is a significant risk of violence against women and LGBTQ individuals. It is crucial that these people’s identity and privacy be protected. Criminals may target charity workers with social engineering techniques in an attempt to learn the names of vulnerable people who get aid from an organization, in addition to pursuing financial gain. I’m not claiming that these companies or people were ever vulnerable to phishing, social engineering, or other illegal activity. I am merely attempting to increase awareness of the significance of data security by presenting a real-world threat scenario.
It should be mentioned that I did not come across any public instances of fraud or misuse that were directly connected to the UN Trust Fund while I was investigating UN Women for this study. Nonetheless, fraud and attempts to get cash from organizations such as the UN or other civil society groups can still occur in any system. Strict supervision procedures are in place to guarantee that monies are distributed correctly, according to the audits and accounting records I reviewed in the non-password-protected database. I do not suggest that UN Women, their partners, associates, funders, recipients, or third-party contractors have committed any illegality, nor do I assert that organization-level or internal data was ever in danger of being misused. It is imperative that all readers perform their own independent security assessments to confirm the correctness, comprehensiveness, and dependability of data protection measures. The fictitious data-risk scenarios I have provided in this study are solely for educational purposes.
I don’t download the information I find because I’m an ethical security researcher. I simply capture a small number of screenshots for reporting and verification. The duration of the files’ public accessibility is unknown because only an internal forensic examination by UN Women or the relevant database management company could determine this information and any possible suspicious activity associated with the incident. Beyond detecting security flaws and alerting the appropriate parties, I don’t do anything else. I also specifically disclaim any liability for any actions that may be done by third parties or others as a result of this disclosure. I don’t do any illegal actions, take advantage of security flaws, or take part in any other activity that could further jeopardize the data. I only share my research to increase awareness of privacy and data security concerns. It is imperative that pertinent parties carry out their own inquiries and implement the necessary security protocols.













